
 oootp
oootp
Legend
Challenge Description
Bob encrypted his sensitive data with one time pad, however we have the suspicion that he did something wrong. We extracted some encrypted data. Note that Bob hates punctuation. Can you decrypt the flag?
c192a8e9e01b95c69c14aae80368c668e97e1f234545beb02ab742c72d0a65043c1c8562d65cd7e462e391a8d50ba04e14d3ac4abe9f09fba4e9f05031b36055509d3bc2e59f18c709f87f
Flag Proof
CTF{b20b26d59d0d4d2f66b69b1cbb5baa089ba8f4379ad24bc32a32fb063c8d16ab}
Summary
Run Many-Time Pad on the file and extract the key to use on the encrypted flag.
Details
We have a hex string that has apparently been encrypted with OTP. Alongside that, we get a file called encrypted_data.txt, which contains a bunch of hex strings.
The title is a hint for the Many Time Pad vulnerability (OTP with many O’s). Basically, the user used the same password to encrypt both the flag and all of the hexstrings from the encrypted_data.txt file. For that, we can use a tool found on GitHub: https://github.com/CameronLonsdale/MTP
Running the MTP script on our encrypted_data.txt file, we get the following:
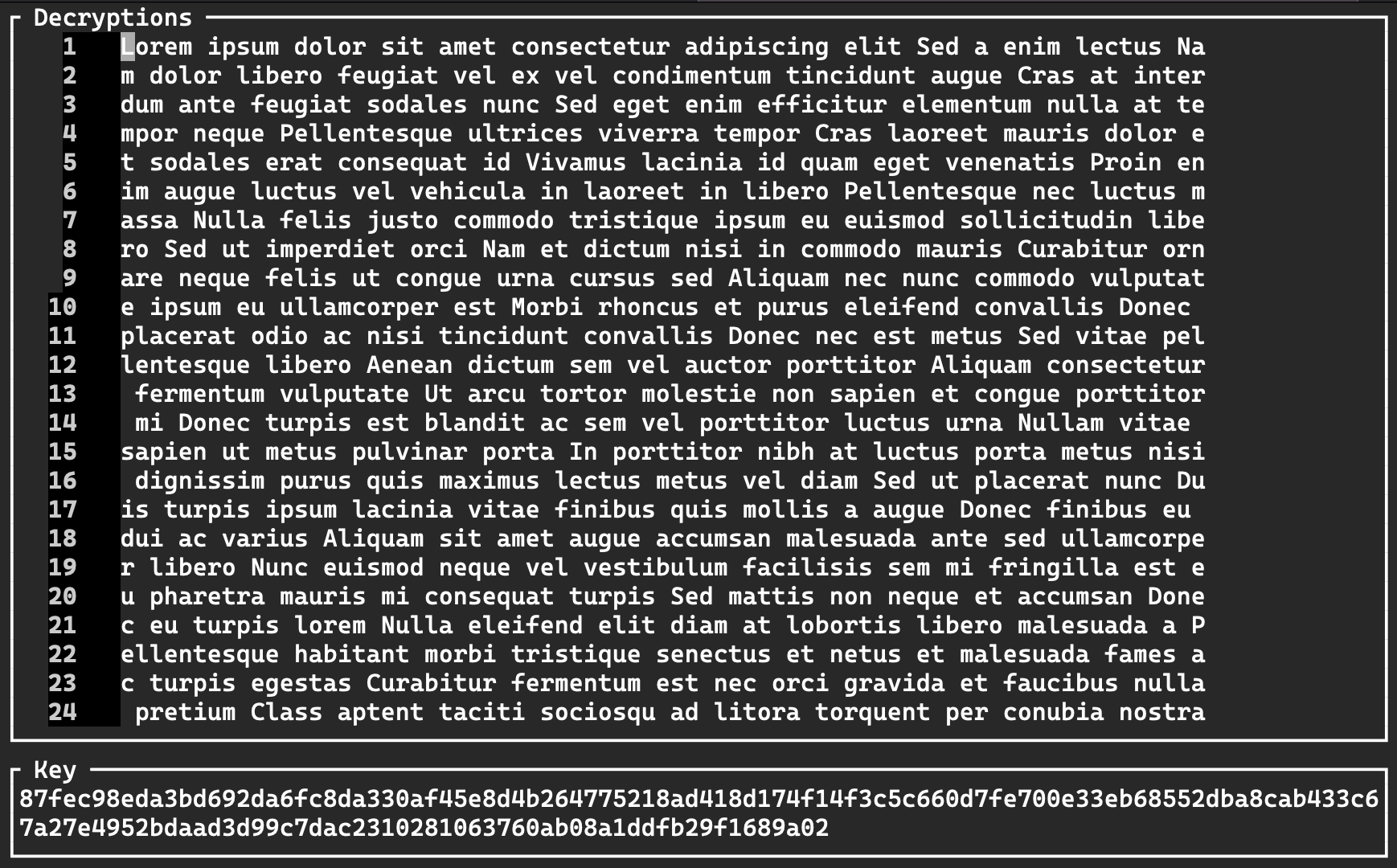
The key at the bottom is the key used to decrypt our flag:
87fec98eda3bd692da6fc8da330af45e8d4b264775218ad418d174f14f3c5c660d7fe700e33eb68552dba8cab433c67a27e4952bdaad3d99c7dac2310281063760ab08a1ddfb29f1689a02
Using this, the given hexstring, and CyberChef, we can decrypt the flag and get:
Flag: CTF{b20b26d59d0d4d2f66b69b1cbb5baa089ba8f4379ad24bc32a32fb063c8d16ab}
